A new phishing email is turning heads, partly because of its seeming legitimacy, and partly because of what the sender threatens to do if you don’t comply. It’s a new twist on an old favourite, but here’s what to look out for so you can protect yourself.
The Hook
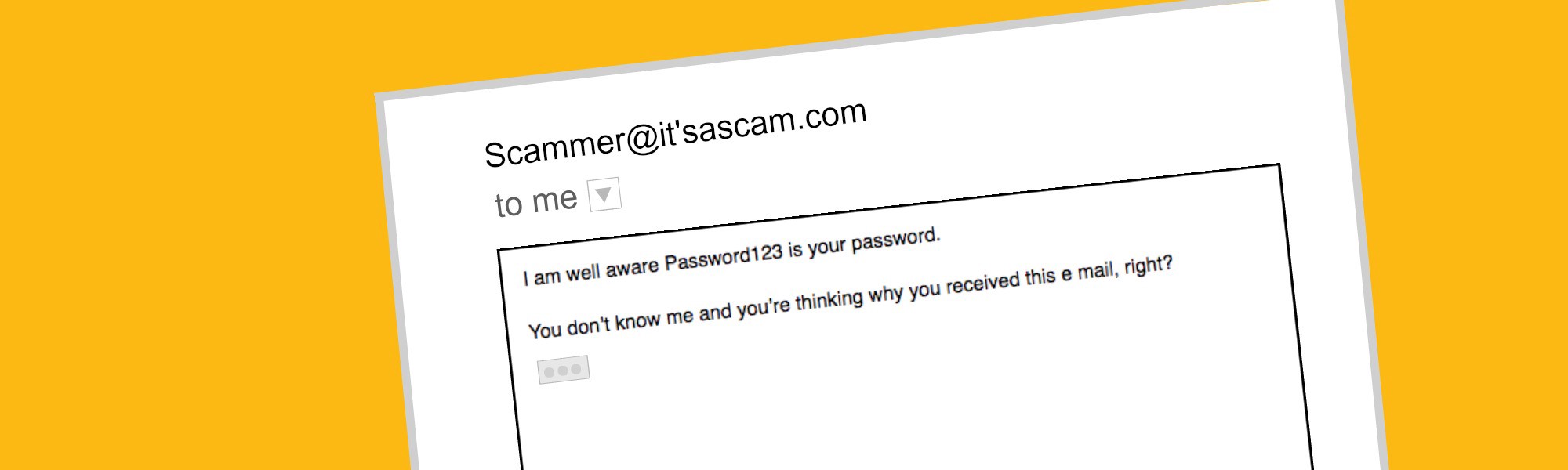
The most unnerving part of this email is that it references an actual piece of information about you, such as a password you currently use, a password you have used, or even a license plate number. That seems to give the perpetrators some credibility, but don’t fall for it. In reality, the scammers have gained a list of usernames, passwords, and other personal details that were compromised in a website data breach, and they’ve now created a script based on that information.
A myriad of websites have been hacked over the years, from Yahoo to LinkedIn. There’s no way of telling which breach these perpetrators are taking advantage of, but you can check if any of your accounts have been involved in a data breach at Have I Been Pwned?
The Threat
Now that they’ve grabbed your attention with your compromised personal information, the perpetrators make their threat. They claim to have installed malware on your computer and have a recording of you watching sexually explicit materials. If you don’t pay their Bitcoin ransom, they threaten to release the video to all of your contacts.
The Scam
This type of scam is called sextortion, a serious crime that occurs when someone threatens to distribute your private and sensitive material if you don’t provide them sexual favours, images of a sexual nature, or money.
Fortunately, the scammers behind this sextortion attempt do not actually have any private or sensitive material to threaten you with. As alarming as this email seems, it’s still a phishing attempt, and recipients should not reply to it or give in to the scammers’ demands.
What to Look Out For
All phishing emails have some common elements that mark them as scams:
- Generic greeting: Perpetrators will know your email address, but will not greet you by name. This is common in phishing emails. If someone had actually installed malware on your computer, they would know a lot more about you than just your email address.
- Spelling or grammar mistakes: Look for poor sentence structure, the grammar mistakes throughout, and misspelled words. These are all clues that point to a phishing email.
- Urgent or threatening language: If the message contains an attempt at blackmail, a 24-hour deadline, and the threat of sending your supposed video recording to five friends, then this all suggests that the message is a phishing attack.
To learn more about how to spot a phishing attack, read To Catch a Phish.
What to Do Next
If you’ve received an email like this:
- Do not reply.
- Do not pay the Bitcoin ransom.
- Check Have I Been Pwned? to better understand which organization(s) the perpetrators may have retrieved your information from.
- Practice good password management, such as immediately changing your password if compromise is suspected, using a strong password, and not reusing the same favoured password across multiple valued accounts. Find more tips on creating strong passwords.
To ensure your information is as safe as possible, consider using a password manager. This will ensure that your passwords are safe in an encrypted cyber vault, and some password managers will tell you when your accounts were involved in a data breach so you can update all necessary passwords.
If you are still unsure or have any other questions, then please contact the Staff Service Centre (contact method updated 2024).

Sheena Moore — Communications Writer, Information Services and Technology (IST)
Sheena is a Communications Writer with Information Services and Technology (IST). She strives to inform the university community about cybersecurity, G Suite, business transformation, and IT initiatives across campus. You can often find her roaming the halls of GSB, searching for grammar mistakes to correct.